
Internet Meltdown: 37.4TB DDoS Attack Slams One IP in Just 45 Seconds!
A Record-Breaking Digital Siege
Internet security giant Cloudflare has announced that it successfully mitigated the largest Distributed Denial-of-Service (DDoS) attack ever recorded, stopping an unprecedented wave of 7.3 terabits per second (Tbps) of junk traffic aimed at one of its clients. In total, the attackers hurled 37.4 terabytes of malicious data toward a single IP address.
At a glance, the data volume might not seem extraordinary, “but the real shock comes from the rate of delivery,” according to The Cloudflare Blog. All 37.4TB of data - equivalent to roughly 9,350 high-definition movies, over 9 million songs, or around 12.5 million high-resolution images - was transmitted in under 45 seconds.
The intensity of the attack highlights just how advanced and aggressive modern cyber threats have become. In less than a minute, the attackers nearly overwhelmed an entire system, illustrating the growing stakes in the cybersecurity arms race.

How the Attack Was Executed
The DDoS campaign employed a multi-pronged strategy, taking advantage of several known vulnerabilities and attack vectors. At its core was a User Datagram Protocol (UDP) flood, a commonly exploited method due to its speed and minimal connection requirements.
UDP, unlike its more reliable counterpart TCP (Transmission Control Protocol), does not establish a connection between two devices before transmitting data. Instead, it simply sends packets without confirming whether the other side is ready or even available to receive them. This design makes UDP ideal for real-time applications like gaming, video conferencing, or live streaming - but also highly susceptible to misuse.
“Because there’s no handshake or verification, attackers can send junk data to every available port on a target system,” Cloudflare explained. As the system tries to respond to each query, its resources are quickly depleted. In this case, the sheer volume of the data rendered any normal processing impossible within seconds.
The Role of Reflection and Amplification
Beyond the raw UDP flood, the attackers incorporated a reflection/amplification component to maximize the attack’s scale. This method relies on spoofing the victim’s IP address and sending requests to third-party servers using outdated or under-secured protocols - like Network Time Protocol (NTP), Echo, or Quote of the Day (QOTD). These services respond, unknowingly, to the victim, amplifying the traffic and overwhelming the target’s bandwidth.
These reflection attacks are particularly dangerous because they allow attackers to use relatively small resources to generate a much larger traffic surge. By multiplying their payload using innocent third-party servers, the attackers can stay hidden while dramatically increasing their impact.

A Pattern of Escalating Attacks
Unfortunately, this wasn’t a one-off event. The history of record-breaking DDoS incidents shows a clear pattern of increasing frequency and scale.
In January 2022, Microsoft reported a record-setting 3.47 Tbps DDoS attack targeting its Azure infrastructure. That figure was soon eclipsed in October 2024 when an East Asian internet provider was slammed with 5.6 Tbps of malicious traffic. Just six months later, in April 2025, Cloudflare documented another assault peaking at 6.5 Tbps and lasting nearly 49 seconds.
These numbers reveal a troubling escalation, with the latest 7.3 Tbps attack demonstrating that threat actors are not only refining their techniques but are also gaining access to more powerful botnets and resources.
The Role of Botnets in Modern Cyber Attacks
At the heart of these attacks are botnets - networks of compromised devices, often consisting of home routers, unsecured servers, smart appliances, and even mobile phones. These devices are unknowingly co-opted into executing attacks on behalf of malicious actors.
What makes botnets particularly concerning is their accessibility. DDoS-for-hire services, also known as “booter” platforms, allow virtually anyone with cryptocurrency and a target to launch large-scale attacks. These services are often advertised in underground forums and are cheap compared to the potential damage they can cause.
Moreover, the financial motivations behind DDoS attacks have grown. Attackers may use such incidents to test vulnerabilities, distract IT teams while launching more targeted intrusions, or to extort online businesses by threatening sustained disruptions unless ransom payments are made.
How Cloudflare Defended Against the Attack
Cloudflare’s ability to intercept and neutralize the 7.3 Tbps assault reflects the strength of its global infrastructure. Its network, which spans over 300 cities and processes trillions of requests daily, is engineered to absorb large spikes in traffic without affecting performance for legitimate users.
Using advanced traffic filtering, rate limiting, and automated mitigation tools, Cloudflare was able to identify and block malicious packets in real-time. “Speed matters in these cases,” the company stated. “We can’t just detect attacks - we have to adapt immediately as they evolve.”

What This Means for Internet Security
While Cloudflare’s response is commendable, the incident underscores a deeper issue: the fragility of internet infrastructure in the face of rapidly evolving cyber threats. As more services move online - ranging from healthcare and finance to education and critical government systems - the impact of a successful DDoS attack could be devastating.
Businesses and public institutions are being urged to invest in robust cybersecurity protocols, including:
- Advanced DDoS mitigation services
- Regular patching of known vulnerabilities
- Strengthened endpoint security
- Traffic analysis and anomaly detection systems
Even individuals have a role to play. Keeping devices updated, avoiding default passwords, and being aware of phishing attempts can reduce the likelihood of becoming an unknowing botnet participant.
Looking Ahead: The Evolving DDoS Landscape
As digital transformation accelerates, so too does the sophistication of cybercrime. The 7.3 Tbps attack is not just a record - it is a warning. The technical ability to generate this level of traffic in under a minute suggests that attackers have more powerful infrastructure and resources than ever before.
Cybersecurity firms, governments, and enterprises will need to stay ahead of the curve - not only to protect their systems but also to prevent global internet disruptions. The race is no longer just about speed; it’s about resilience, adaptability, and strategic foresight.
Cloudflare's success in halting the attack shows that it’s possible to defend against even the most aggressive threats - but it also raises the stakes for everyone else. The next attack might be even faster, larger, and more coordinated. The question is: will the next target be ready?
News in the same category


Mosquitoes Rain From The Sky Over Hawaii—Scientists Explain Why

Nasa Tracks Plane-Sized Asteroid Speeding Toward Earth At 47,000 Mph

Two-Year-Old Boy Bites Cobra To Death After Snake Coils Around His Hands In India

Four Famous Psychics Warn World War III Could Begin By End Of 2025

Eat Just 3 of These Daily and Watch What Happens to Your Body
. Their ability to benefit nearly every major system in the body - from the heart and liver to the brain and bones - makes them a powerful ally in maintaining health and vitality.

Psychic who suffered near-death experience reveals shocking truth about the afterlife
A psychic has detailed about afterlife after claiming to have experienced the feeling "dea@th" four times.

Real story behind Amelia Earhart and the Bermuda Triangle as scientists 'solve mystery' after 88 years

Airlines forced to cancel flights after 'Japanese Baba Vanga' predicts catastrophic disaster

8.7 magnitude earthquake off Russia: Japan experiences first tsunami, many countries issue warnings

Google Maps Solves Chilling Mystery of Missing Woman - Captured Her Final Moments by Accident
The story resurfaced in a video uploaded by a YouTube channel, sparking a wave of disbelief and emotion online.

What Causes Those Strange Ripples In Your Jeans After Washing?
Terrifying Truth Behind Mysterious ‘Circle Of Bubbles’ In The Ocean Revealed

People Stunned After Learning The True Meaning Behind ‘SOS’ — It’s Not What You Think

After Spending 178 Days In Space, Astronaut Shares a ‘Lie’ He Realized After Seeing Earth

People Shocked To Learn What The Small Metal Bump Between Scissor Handles Is Actually For

Scientists Use AI And Ancient Linen To Reveal What Jesus May Have Truly Looked Like

Earth may witness a once-in-5,000-year event on the moon and it's coming sooner than you think
AI is willing to kill humans to avoid shutdown as chilling new report identifies 'malicious' behaviour
News Post

She held on, certain they would come back. Yet as days turned into weeks, her strength waned—until a fresh kind of love unexpectedly entered her life.

The Hidden Light In Your Hands That Shouldn’t Be Dimmed

Mosquitoes Rain From The Sky Over Hawaii—Scientists Explain Why

Doctor Shares 30-Second Hand Test That Could Reveal Hidden Brain Tumor

Nasa Tracks Plane-Sized Asteroid Speeding Toward Earth At 47,000 Mph

Groundbreaking Research: Reversing Memory Loss In Alzheimer’s Disease Without Removing Plaques

Rfk Jr. Raises Health Concerns Over 5G, Says It May Affect Brain Function And Cancer Risk

Two-Year-Old Boy Bites Cobra To Death After Snake Coils Around His Hands In India

Four Famous Psychics Warn World War III Could Begin By End Of 2025

Abandoned puppy was found in terrible shape — see his incredible transformation one year later in the comments 🥹

Eat Just 3 of These Daily and Watch What Happens to Your Body
. Their ability to benefit nearly every major system in the body - from the heart and liver to the brain and bones - makes them a powerful ally in maintaining health and vitality.

Psychic who suffered near-death experience reveals shocking truth about the afterlife
A psychic has detailed about afterlife after claiming to have experienced the feeling "dea@th" four times.

Blood Type O Diet: What to Eat and What to Avoid

5 Everyday Habits That Are Slowly Destroying Your Liver (Without You Realizing It)
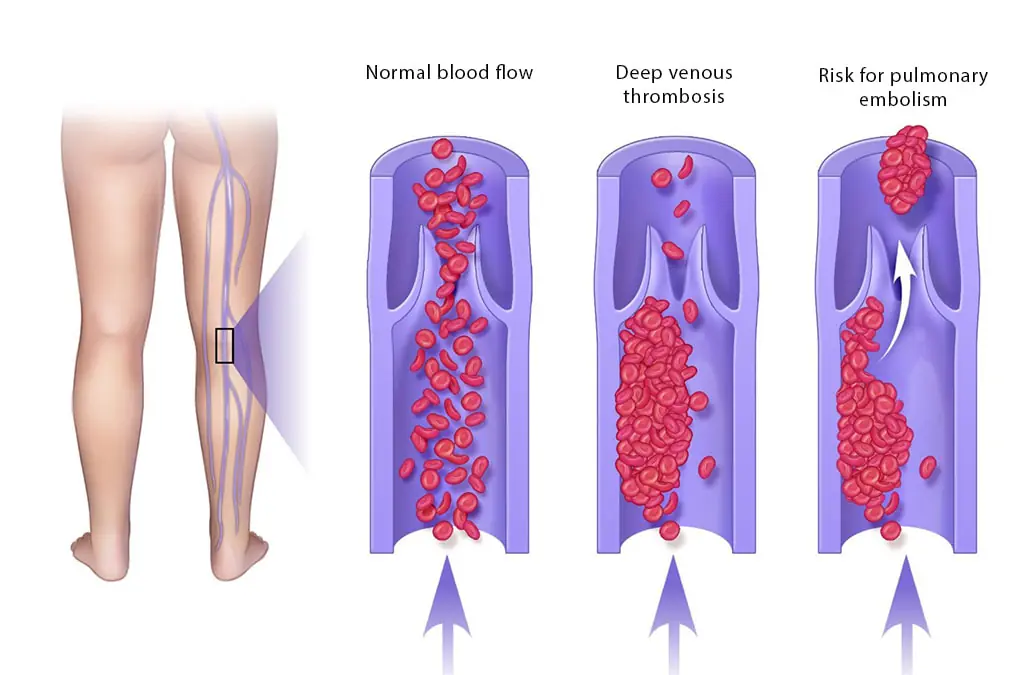
Blood Clot in Leg: Signs and Symptoms You Shouldn’t Ignore

Real story behind Amelia Earhart and the Bermuda Triangle as scientists 'solve mystery' after 88 years

Airlines forced to cancel flights after 'Japanese Baba Vanga' predicts catastrophic disaster

8.7 magnitude earthquake off Russia: Japan experiences first tsunami, many countries issue warnings

After Seeing Her Husband's Photo with a Pregnant Stranger, Nadya Chose Silence – But What Happened Next Was Sh0cking
It was unthinkable! How could this be happening? Nadezhda thought, staring at a photograph of a young pregnant woman sitting on her husband’s lap, smiling, and clinging to him. Twenty-five years of marriage... and now this? Her heart tightened painfully

I Went Undercover as a Homeless Person to Test My Granddaughter's Fiancé – What I Found Was Beyond Sh0cking
I dressed in old, ragged clothes, hid my face beneath a weathered hat, and stood on the street like a beggar—just to see what kind of man my granddaughter was marrying. I thought I was prepared for anything, but what happened next left me speechless and